Table of Contents
Introduction
In this article I would like to give a few hints on improvements and actions to perform a light bastioning of the digital environment in our home. A widely used improvement method is to identify patterns of problems, in order to address them at common points.
When we talk about the digital security of a home, we can think of several:
- Outgoing connections, which download data from external machines.
- Network cabling, and in a larger instance, wireless networks, which are interoperable from outside the physical environment of the home.
In the following points I will briefly describe some of the ways in which software can help us at these points. Some of them may not be the typical security and control measures that we will no doubt already have in place.
DNS
One of the entry points for possible malicious elements in our home digital environment is to navigate to pages with dangerous links or outright dangerous links. Although many current browsers and antiviruses have functions to block this, it is usually in the context of each device.
One option we can consider is Pihole.
Pihole is a self-hosted DNS system that allows blocking, by means of lists, the connection to domains known to host threats.
Although I won’t go into the details of the installation, I will comment that in addition to being able to install it on a low-power PC, such as a raspberry pi, it can also be used as a docker image.
The operation of Pihole is simple, once installed, we can enter the ip of the machine/docker and we will have a dashboard with results by client device, most blocked addresses, % of blocked calls over total calls, to give some examples.
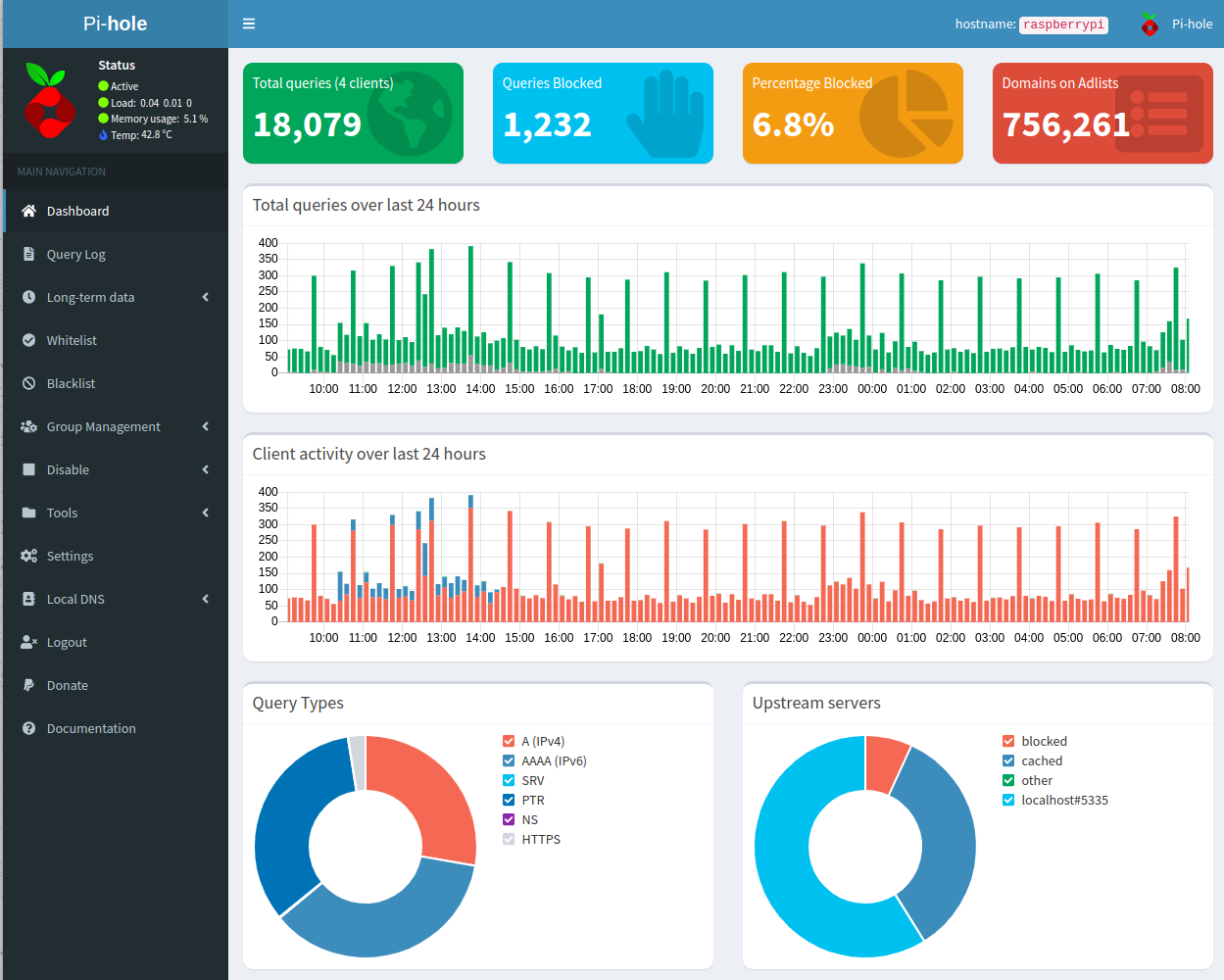
For all the devices in the house to use Pihole, it would be enough to tell our router to use its ip address as DNS server.
VPN
As with professional infrastructure systems, we can benefit from having devices that are physically remote under the cloak of our local network security. An example of this would be our mobile devices when we are out and about.
One option to do this is to install a VPN at home and connect to it from outside.
In this case my recommendation is to install on the same machine where we have installed Pihole, another service called PiVPN. The installation process can then recognise that there is a PiHole installation and configure it so that the DNS filter also works with the devices that connect via the VPN.
Regarding the type of VPN, it is allowed to install:
- OpenVPN: This is an old, but robust VPN. It is difficult to maintain by the developers because the code is immense.
- Wireguard: This is a modern VPN that tries to replace OpenVPN. It is also optimised to use less battery power on mobile devices.
I’ve had OpenVPN at home for years with no problems, until I recently changed the installation to Wireguard (which is the one I recommend because it’s faster to create a client configuration, native mobile app, and low battery drain).
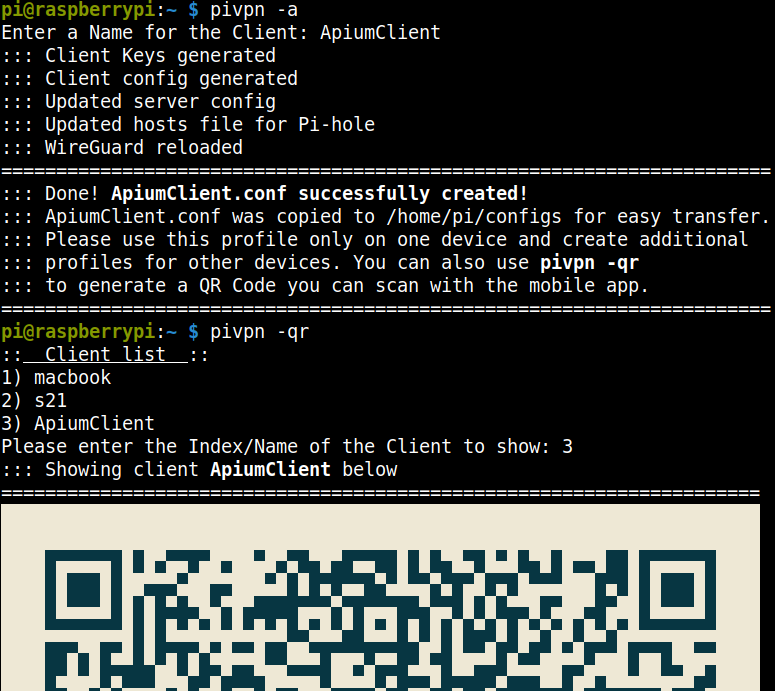
Creating a new client with wireguard is relatively simple, and you can scan a QR code with the official mobile app to import the data automatically:
Wireless Networks
As a first comment, one of the things we can forget about wireless networks is that usually wireless access points allow you to configure the power of the antennas. If we can connect to our Wifi from the street, anyone can carry out attacks on it. In this case we should lower the power of the access point.
Another idea, some products allow monitoring and detection of foreign devices on the network, but if you don’t want to rely on them, it is quite easy to set up a process that performs periodic scans.
This would be a sketch (not production ready!) in kotlin to run nmap on the local server (assuming a linux machine with nmap installed) and extract a list of devices:
fun deviceDetection() {
val process = ProcessBuilder("nmap", "-sn", "192.168.1.0/24").start()
process.inputStream.reader(Charsets.UTF_8).use {
val devices = it.readText()
.lines()
.filter { it.contains("192.") }
.stream()
.map { parseDevice(it) }.collect(Collectors.toList())
// Your code goes here
}
process.waitFor(10, TimeUnit.SECONDS)
}
fun parseDevice(line: String): Device {
val baseValue = line.replace("Nmap scan report for ", "")
.replace("(","")
.replace(")","")
.split(" ")
return Device(
baseValue[0],
baseValue[1]
)
}
data class Device(val name: String, val ip: String)
A possible further use of these devices would be to save the results in a DB and notify in some way (email, telegram message) if a new device is detected.
Another possible evolution, more complex, would be to notify with a question, so that the program will notify the local network system (a software router for example) if the user wants to block the newly detected device.
Conclusion
These are some ideas to increase security and decrease the attack surface on our home infrastructure. Once implemented, the improvement is noticeable.
However, there are a few more measures, if we want to get into “paranoid” territory, which I will touch on in later articles 🙂
Author
-

Professional with more than 13 years of experience in software development focused on the back-end area using Java and Kotlin.
View all posts









