Table of Contents
In HTTPS for Dummies article, we will see what HTTPS is and why that final S is so important.
Let’s start with the basics. HTTP is a communication protocol and HTTPS is HTTP with a security layer that adds confidentiality and more security properties.
HTTPS for Dummies: asymmetric encryption
Asymmetrical cryptography is based on a coding of information based on two keys, a private and a public one. As their names indicate, the private one must be kept by the sender and the public one can be delivered to any receiver. With the private one, we can decrypt all the encrypted messages with the public key and with the public one we can only decrypt the encrypted messages with the private key.
1.Public key cryptography
Just like I mentioned, the public key can encrypt messages which later on will only be decrypted with the private key. This means that nobody with the public key can decrypt that message.
Like this we get confidentiality. The sender has encrypted the message with the public key of the receiver, so nobody except the receiver will be able to interpret the message.
2.Encrypt with the private key (digital signature)
With the private key, we can encrypt information that can be read by anyone who possesses the public key pair to the private one. This process does not give us confidentiality (since anyone with the public key could read the message), but we achieve authenticity and integrity.
We get the authenticity because only the one with the private key can encrypt the information the way that only the one with the public key is able to decrypt it.
We also force the non-repudiation of the message, the sender could not tell you that this message is not his one, since only he has been able to encrypt it.
Integrity is achieved in the moment when only the one that encrypts the message with the private key gets a package capable of being decrypted by the public key, and nobody is capable of decrypting it, modifying it and re-encrypting it again if you do not have the private key.
HTTPS for Dummies: symmetric encryption
It is important to know that there is also the concept of symmetric encryption. It is more basic than the asymmetric one, but it plays an important role in a client-server communication using the HTTPS protocol.
The difference is that symmetric encryption is based on a single key, both to do the encryption and the decryption. Authenticity and confidentiality are not achieved, but on another hand it is much cheaper and involves the sharing of the key between sender and receiver.
HTTPS for Dummies: SSL Certificate
According to Wikipedia, a (digital) certificate is: “a computer file that is generated by a certification services entity that associates identity data with a physical person or company, thereby confirming their digital identity on the Internet.” So far we have the mechanisms for a person or an organization to encrypt a message and show that it is theirs. However, we do not know who they are, and how to know that the message is from Google, Facebook or Random Herbalism.
Here comes the concept of CA (Certificate authority or Certification authority), is an entity responsible for verifying the identity.
The process to request a certificate is simple, the organization must generate a CSR (certificate request), send it to the CA, once this information is valid, a certificate is generated based on that digitally signed CSR and then it is sent to you, easy right? But what is a CSR?
A CSR is a block of text that contains information about the applicant such as the name of the domain, name of the organization, city, email, etc. and the public key. This CSR must be digitally signed and sent to the CA. The CA, together with the CSR, will find the public key with which to decrypt that message and validate the data. When the CA confirms that you are who you say you are, they send you that same certificate but digitally signed by them.
At this point the only thing that we need to understand is that these CAs are entities in which our operating systems or even applications rely on series (they have the public key of those CA), if a company like GoDaddy or Comodo issues you a digitally signed certificate by them, all computers will trust that this information is valid.
HTTPS for Dummies: how does HTTPS work?
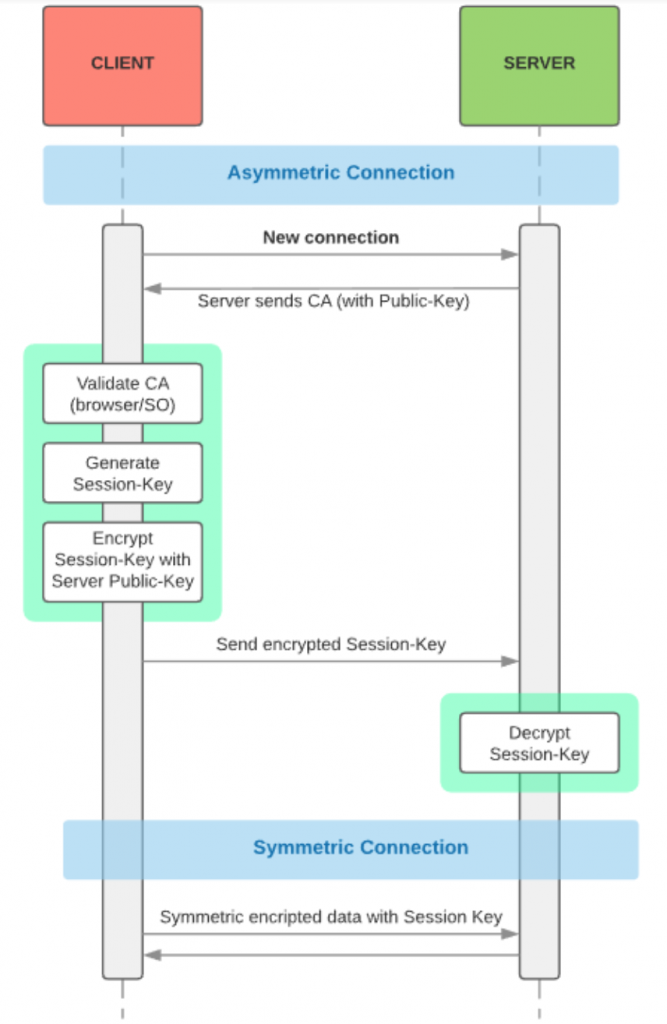
We have already seen all the necessary elements to have an HTTPS communication, now we have to combine them. What we are going to do is exchange a key to use a symmetric encryption (performance) between client / server using asymmetric encryption (security).
The process in broad strokes is simple, the first communication is for the server ( sender) to send the certificate along with the public key to the client (receiver). The client generates the “secret” that will be used for communication with symmetric encryption, encrypts it with the public key and sends it to the server, and it ensures that only the client / server has this key.
Once the server decrypts the message with the session-key, symmetric communication can begin safely, since the key is only valid for one session at a certain time.
I hope you found this article useful!
Good luck, guys!
If you found this article about HTTPS for dummies interesting, you might like…
Charles Proxy in Android Emulator
Callback hell Nodejs: a solution with Fiber
Singles responsibility principle in object-oriented design
A guide to Tmux that will increase your productivity
Scala generics I: Scala type bounds
F-bound over a generic type in Scala
Microservices vs Monolithic architecture
Author
-
Software developer with over 16 years experience working as Fullstack Developer & Backend Developer.
View all posts